OKTA
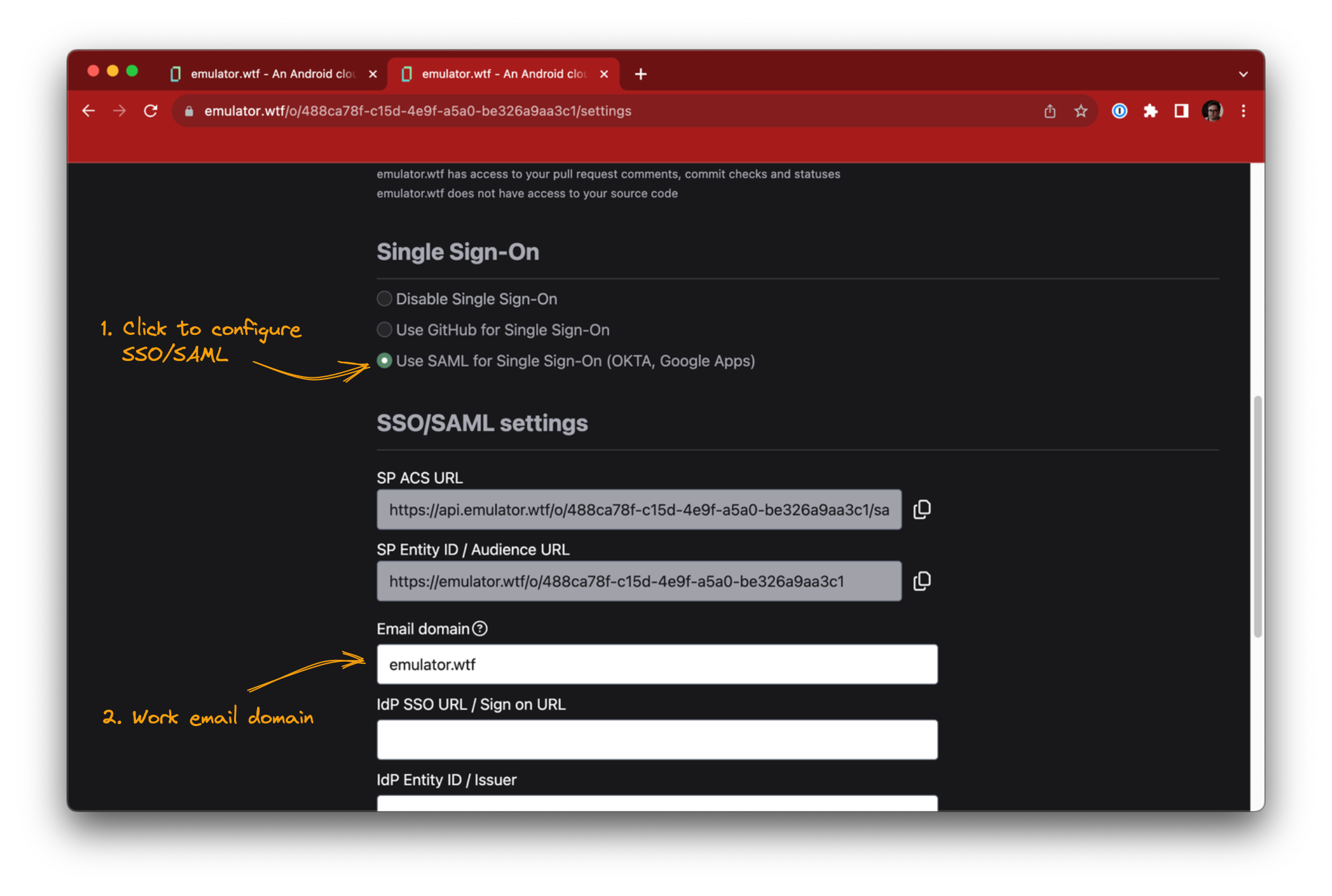
Start configuring SSO/SAML from the Settings page in emulator.wtf web app, scroll to the SSO/SAML section and click Use SAML for Single Sign-On.
Check that you have a configured email domain for your organization, this will be used by your user accounts to sign in with SSO/SAML. If you don’t have a configured email domain then contact support.
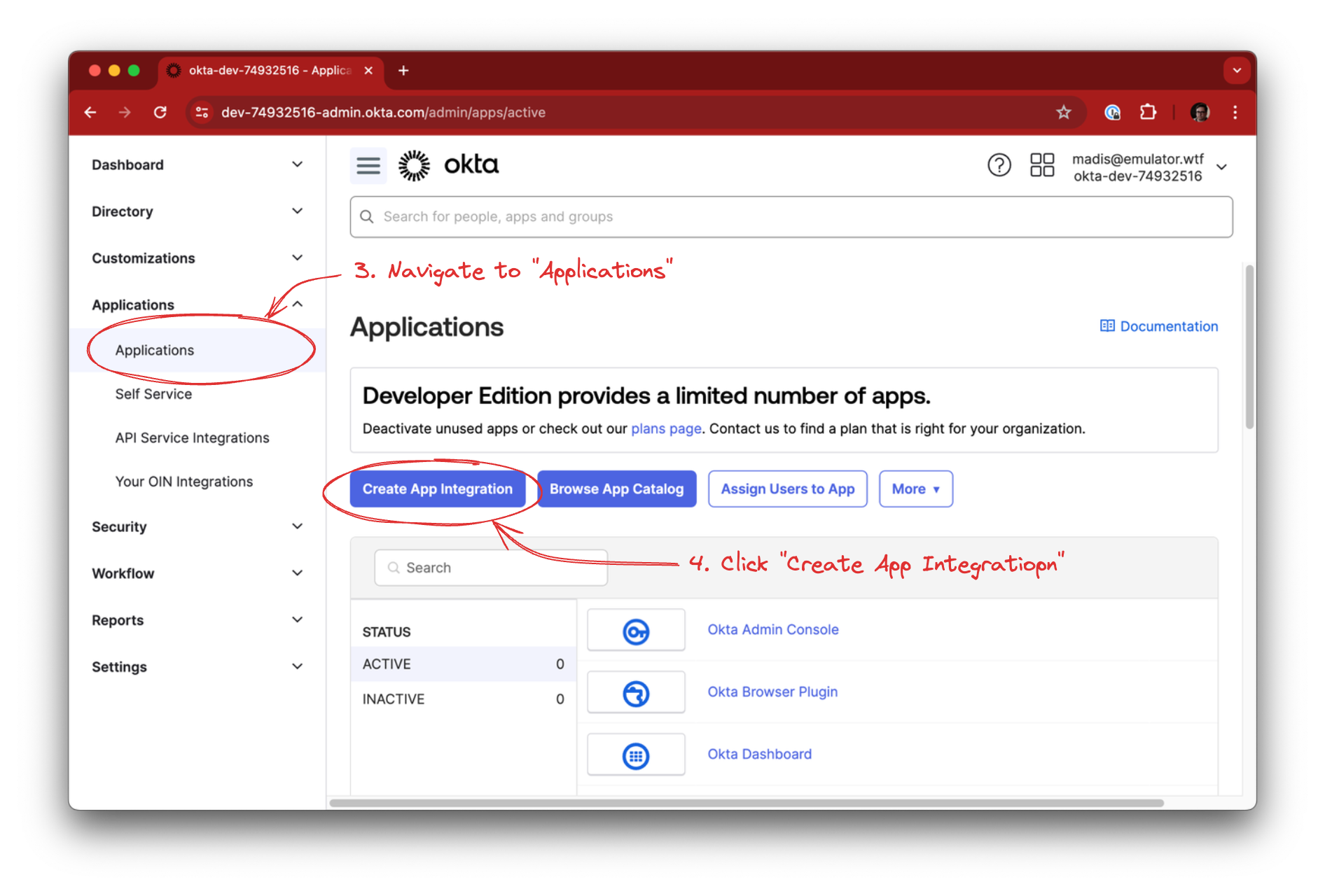
In OKTA, navigate to Applications -> Applications and click the Create App Integration button.
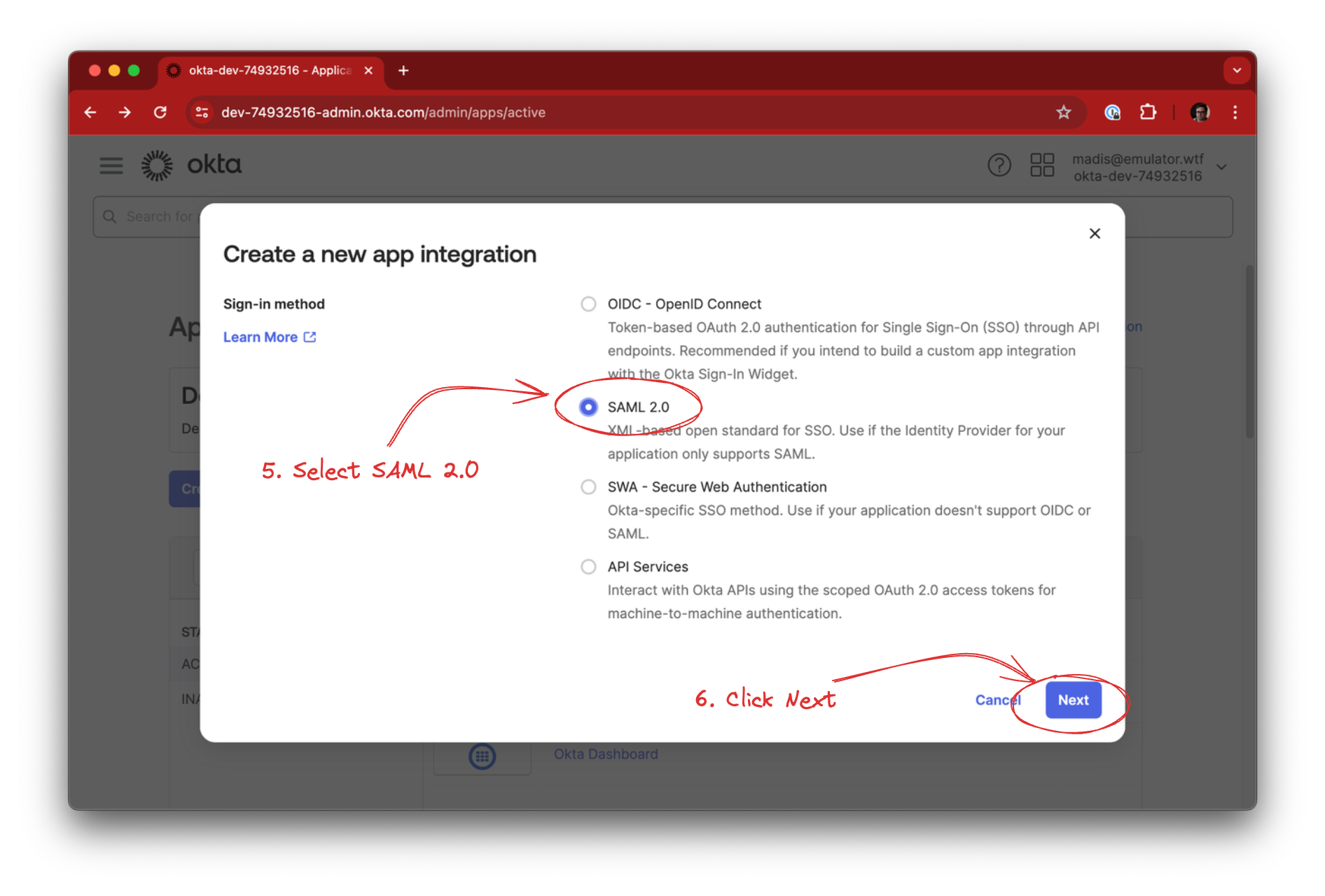
Select SAML 2.0 as the Sign-in method and click Next.
Fill in the App name, optionally the logo, and click Next:
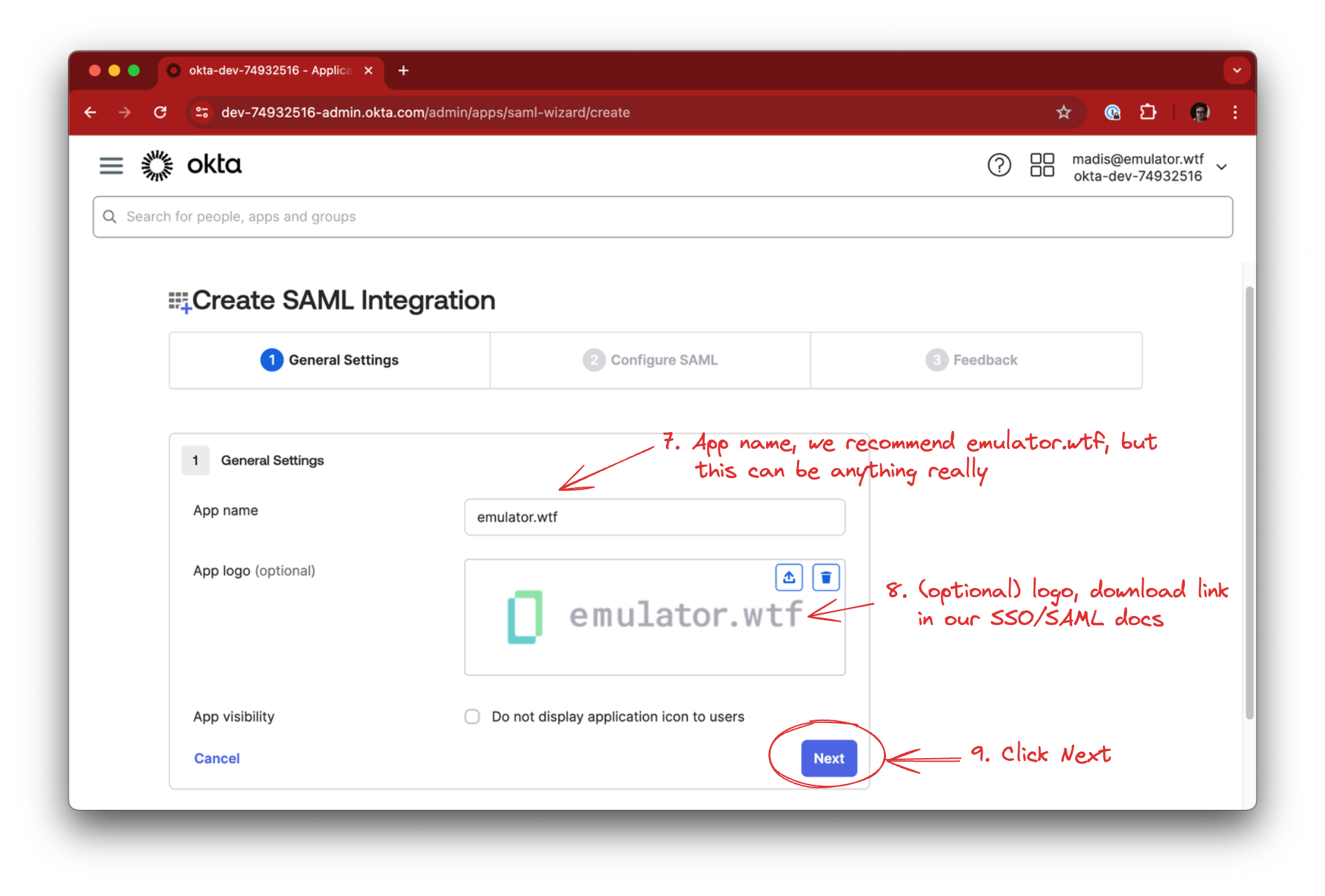
You can use this for the emulator.wtf logo:

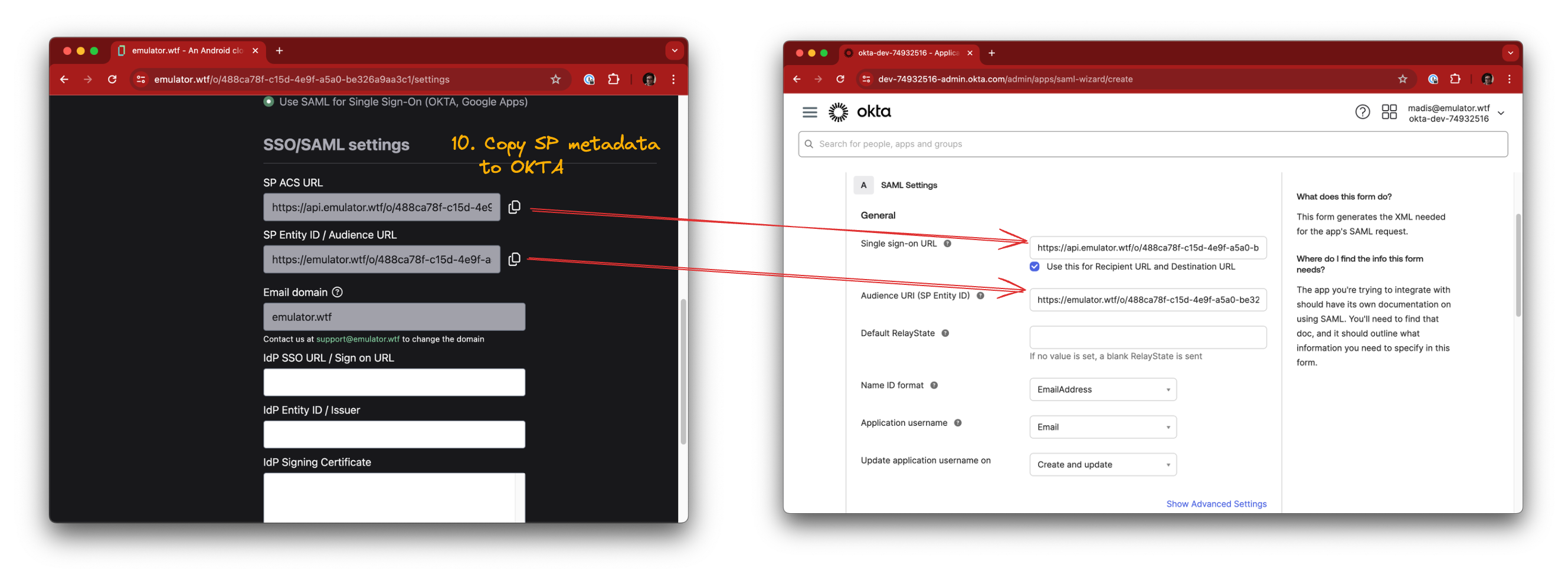
Copy over the following fields from emulator.wtf SSO configuration into OKTA:
- SP ACS URL -> Single sign-on URL
- SP Entity ID / Audience URL -> Audience URI (SP Enttiy ID)
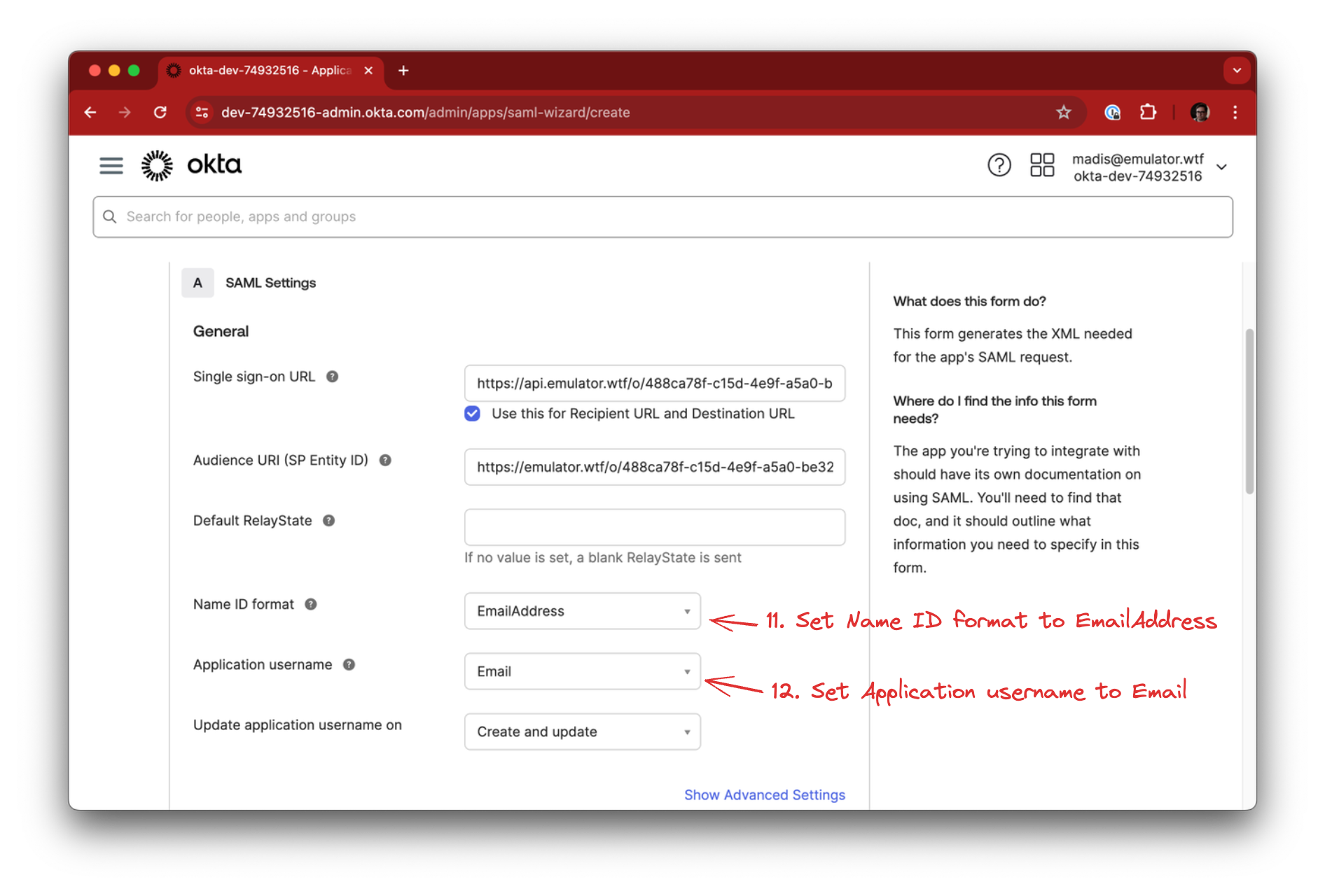
Fill in a few additional details for wiring user accounts:
- Set the Name ID format to EmailAddress
- Set the Application username to Email
Proceed by clicking Next.
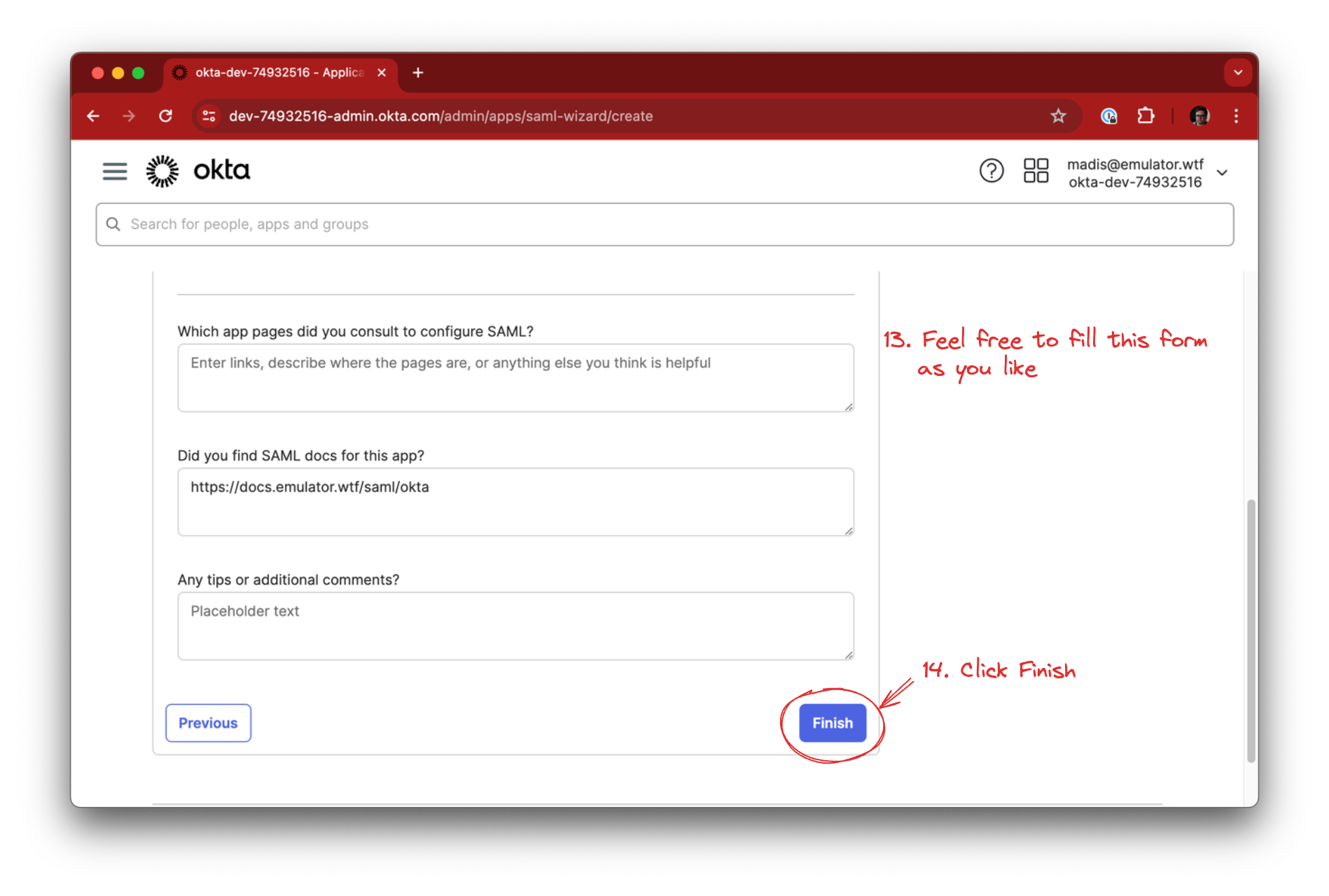
In the feedback section you should leave the This is an internal app… and It’s required to contact… options unchecked.
In the Did you find SAML docs for this app? field you could use the link of this document - https://docs.emulator.wtf/saml/okta.
Click Finish.
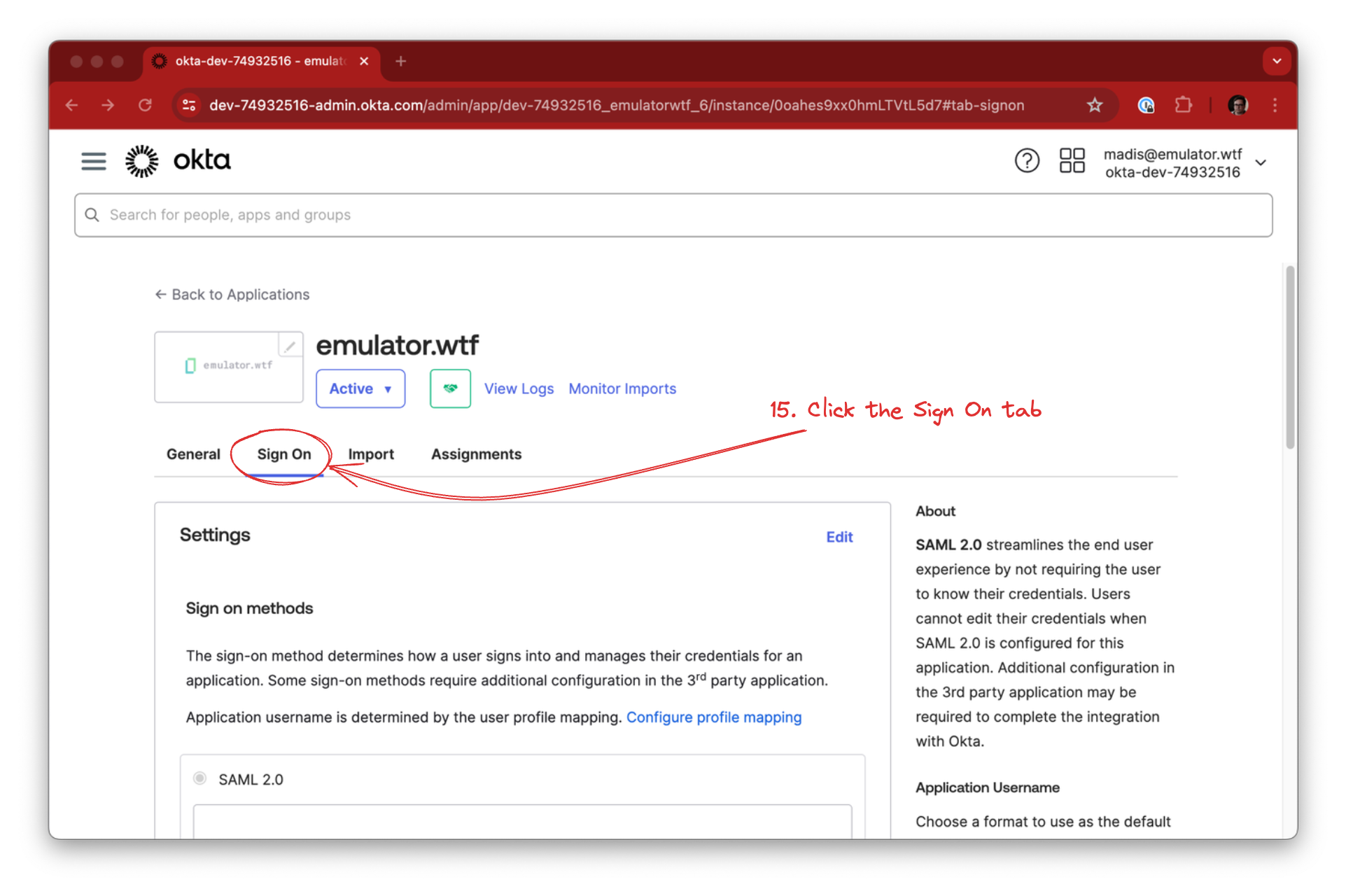
Now that OKTA knows about emulator.wtf we need to do the reverse as well - tell emulator.wtf about the OKTA integration you just created.
In the OKTA application, click the Sign On tab and…
…expand the SAML 2.0 details by clicking More details in the SAML 2.0 section.
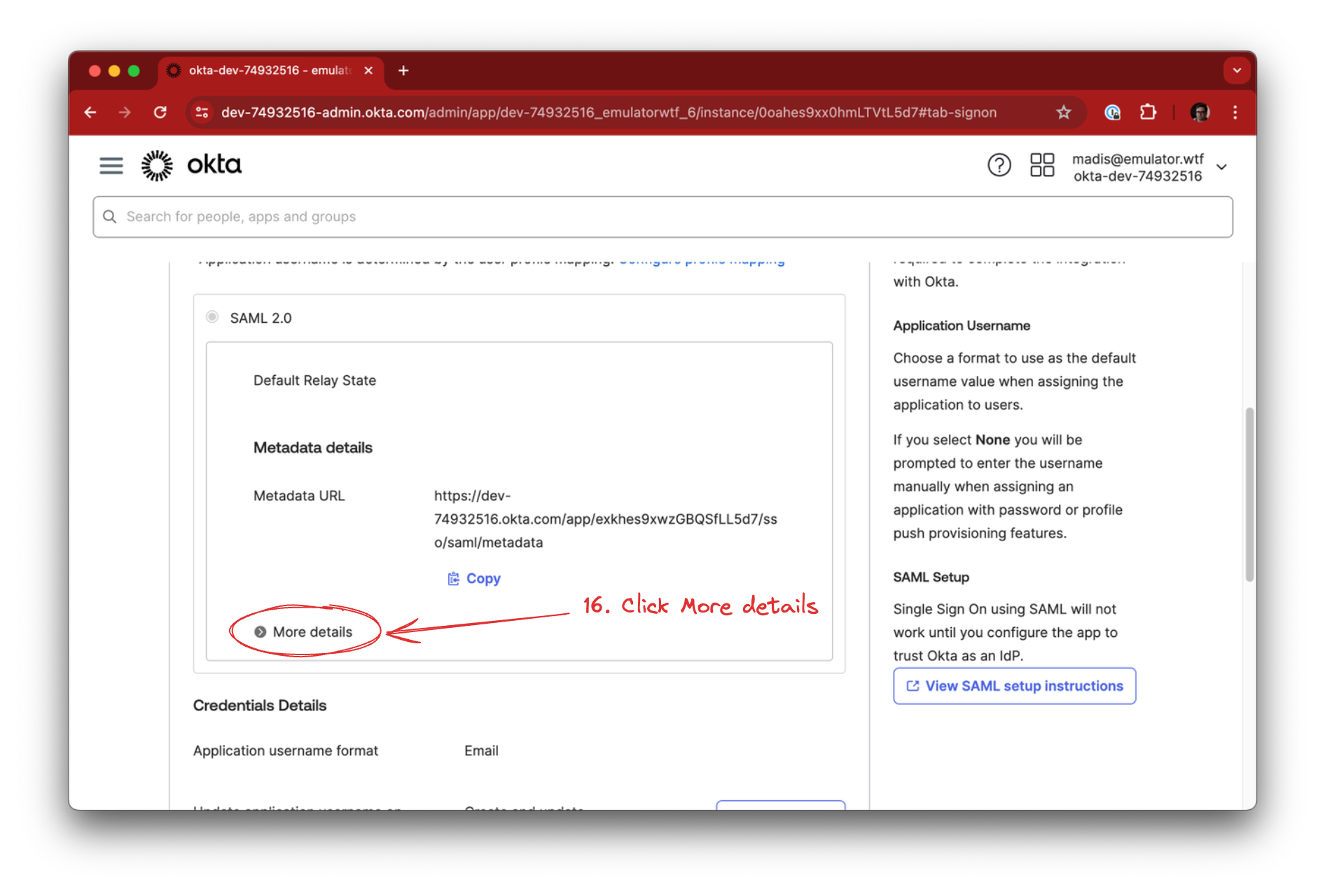
Copy the following from OKTA into emulator.wtf SAML configuration:
- Sign on URL -> IdP SSO URL / Sign on URL
- Issuer -> IdP Entity ID / Issuer
- Signing Certificate -> IdP Signing Certificate
Click Configure to finalize SAML configuration in emulator.wtf.
You’ll also need to assign a group or a list of users to the emulator.wtf application. This depends on your OKTA structure, but you might have a group such as Mobile Developers or Engineering that could be a good fit.
Start by going to the Assignments tab, click on the Assign dropdown and select Assign to Groups.
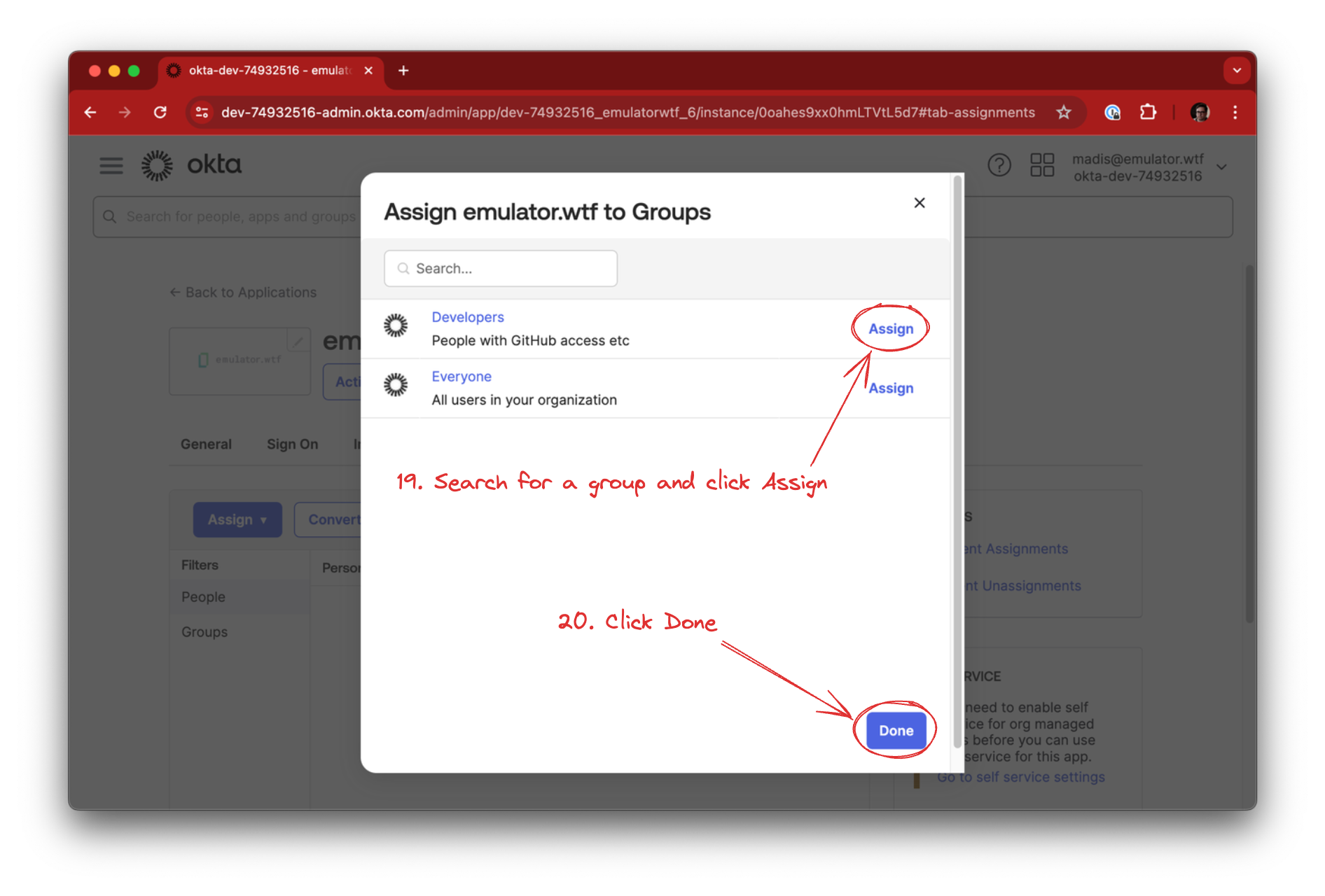
Add the group you want to give emulator.wtf access by searching for it and clicking the Assign button. When all groups have been added, click Done.
SSO/SAML with OKTA is now enabled for your organization! 🎉